Link Script:OptimizeVHDs.ps1
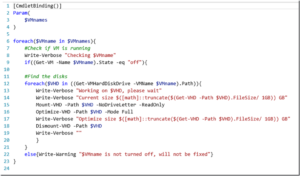
Fonte: https://deploymentbunny.com/2015/06/15/powershell-is-king-compress-compact-optimize-vhd-and-vhdx-files/
Link Script:OptimizeVHDs.ps1

Fonte: https://deploymentbunny.com/2015/06/15/powershell-is-king-compress-compact-optimize-vhd-and-vhdx-files/
1 – Reiniciar a VM e pressionar F8 para entrar em um menu do Windows de seleção de método de inicialização; (no caso da VM, foi necessário entrar via Host, e deixar a VM em modo “Tela Cheia”, para que o F8 fosse interpretado pela VM).
2 – Selecionar a opção Directory Services restore mode;
3 – Irá iniciar a interface gráfica, mas em modo de segurança. Logar com a conta do administrador (local, não no AD);
4 – Abrir o prompt de comando (cmd); Digite então:
cd \windows\system32
NTDSUTIL
Dentro do ntdsutil, digite:
activate instance NTDS
files
Dentro do files, se ainda não deu erro, digite:
checksum
Provavelmente dará um erro, saia então do “files”:
quit
Saia também do ntdsutil
quit
5 – Após verificar o erro, vamos realizar um backup do arquivo ntds.dit antes de mexer nele:
cd\
md backupad
cd \windows\ntds
copy ntds.dit c:\backupad
cd \windows\system32
6 – Rodar então o comando para checar a integridade:
esentutl /g c:\windows\ntds\ntds.dit
7 – Provavelmente o comando anterior retornará um erro. Rodaremos então o comando abaixo para tentar recuperar o arquivo corrompido:
esentutl /p c:\windows\ntds\ntds.dit
Clicar em OK/Aceitar na janela que abrirá.
8 – Copiar os logs (também é possível excluí-los, se for o caso)
cd \windows\ntds
move *.log c:\backupad
9 – Neste momento, a recuperação já deve ter sido realizada com sucesso. Vamos testar:
cd \windows\system32
ntdsutil
Dentro do ntdsutil:
activate instance ntds
files
Dentro do files:
info
Provavelmente mostrará as informações corretamente. Também é possível testar novamente com o checksum, que também deverá rodar com sucesso desta vez.
10 – Como ultimo teste:
Saia do “files”:
quit
Ainda dentro do ntdsutil:
Semantic Database Analysis
Dentro do console que entrar, digite:
Go
Deve rodar sem apresentar nenhum erro.
11 – Após isso, a VM pode ser reiniciada. Ao iniciar novamente, deve subir ok.
Créditos: http://toor.com.br/windows-server-2012-0xc00002e2/
So in order to resolve this issue, open command prompt with Administrative Rights. You can do that by right clicking on CMD and then click on “Run as Administrator”. Change the default directory to C:\Windows\System32
Once you do that, type the following command.
dir /a /S *.MOF
This command will search all the .mof files. It is the file format for Windows Management Object files. WMI data (such as definitions of namespaces, classes, instances, or providers) are sometimes represented in MOF files.
Now change the directory path to wbem by typing CD Wbem and then cd AutoRecover.
now type this simple command
for /f %s in (‘dir /b *.mof *.mfl’) do mofcomp %s
and hit enter.
Créditos: https://www.youtube.com/watch?v=NxOr_HMJaxg
sc queryex servicename
taskkill /f /pid [PID]
Créditos: http://www.examiner.com/list/how-to-kill-a-windows-service-that-s-stuck-on-stopping-or-starting
Vamos abrir o Exchange Management Shell e digitar o seguinte comando:
Get-MailboxDatabase –Identity <Nome da database desejada> | Add-ADPermission –user <Nome do usuário que terá a permissão em todos os Mailbox> –AccessRights GenericAll
Créditos: http://diogoheringer.com/2012/02/15/full-access-permission-todas-as-mailbox/
Baixar e instalar o Microsoft Online Services Sign-in Assistant e Install Windows Azure AD
For single user
Connect to Windows PowerShell using Admin credentials
Connect-MsolService
Set-MsolUser -UserPrincipalName <user ID> -PasswordNeverExpires $true
For all users
Get-MSOLUser | Set-MsolUser -PasswordNeverExpires $true
How to check whether the password is set to never expire
For single user
Get-MSOLUser -UserPrincipalName <user ID> | Select PasswordNeverExpires
For all users
Get-MSOLUser | Select UserPrincipalName, PasswordNeverExpires
Créditos: https://dilshansaminda.wordpress.com/2014/08/05/office365-setup-user-password-to-never-expire/
Well this tutorial shows you how to hack any Admin account or any privilege account on any WINDOWS based operating system.
Press shift key 5times or more, you will see a sticky key option, this has a name as sethc.exe in the system32 folder of windows directory.
for this whole process we need administrative privilages to allow modifications in the system32 folder for windows vista or Windows 7 so inorder to gain that access remotely follow the parameters :
Steps to do this using Command Prompt :
1. Open command prompt with administrative privileges and type in the following :
cd\
c:\cd windows\system32
c:\windows\system32> takeown /f sethc.exe
(this command basically gives you the ownership to that particular file. Now we have to gain administrative privilege on that file to do that -)
c:\windows\system32> icacls sethc.exe /grant administrators: f
now do this again for cmd.exe file :
c:\windows\system32> takeown /f cmd.exe
c:\windows\system32> icacls cmd.exe /grant administrators: f
Now as we have control on both the files follow these :
1. Delete or rename sethc.exe with someother name.
2. Make a duplicate copy of cmd.exe file and then rename it with “sethc.exe” without quotes.
3. Now ensure that you have 2 copies of cmd.exe, one is the original cmd.exe file and the other which is renamed as sethc.exe
Now when you press shift 5times or more you get a command prompt instead of a sticky key window prompt.
now you can use this command prompt to gain access to that computer as follows:
Now when you have replaced that duplicate cmd with sethc.exe command prompt will appear as soon as you press the shift key 5times or more do this at the time of logon.
When the console asks you for the password press shift key 5times or more to get the command prompt.
Now type in the following :
net user <username> * (Press enter it will ask you for a password)
for example my username is Admin:
net user admin *
type a new password :
confirm password :
fill it blank and you have reset the password of that account. Now type “exit” without quotes to get out of the command prompt and select the arrow button of windows vista/7 or press enter for windows xp to bypass the login screen.
Extreme users can use the above replacement of sethc.exe with cmd.exe without having to logged in to the computer. Nube skill users can use it in logged in computers.
Créditos: http://hackinfoworld.blogspot.com.br/2011/01/sticky-keys-and-command-prompt-hack.html
netdom query fsmo
# sc queryex servicename
# taskkill /f /pid [PID]
Créditos: http://www.examiner.com/list/how-to-kill-a-windows-service-that-s-stuck-on-stopping-or-starting
DSQUERY user "OU=myOU,OU=myUsers,DC=myDomain,DC=loc" -limit 0 | DSMOD user -pwd <insert new password here>
Outros comandos mais usados.
http://windowsitpro.com/powershell/top-10-active-directory-tasks-solved-powershell
